How to deal with uncertainty if you build or work with a CRQ model?
Developing a model for Cyber Risk Quantification (CRQ) is a challenge, especially if you want to include unknown risks. When you present results from a CRQ model, typical questions are:
- “How can you predict the future behavior of hackers?”
- “How do you include blind spots or ripple effects in this large complex organization?"
- “How do you generate the frequency and severity parameters if you don’t have enough data?”
The two main problems are:
- How do you know you are assessing all the risks that are pertinent to you (at least the material ones)?
- How do you get sufficient data to assess the risks you do know about?
If you are not taking everything into account or not accurately assessing risks you could end up uncomfortably surprised when something bad happens that you didn’t plan for.
In this blog I will explain how we at Squalify are using different strategies to address different types of unknown risks.
To better structure this problem we use the “Rumsfeld Matrix” to categorize risks into Known-knowns, Known-unknowns, Unknown-knowns and Unknown-unknowns:
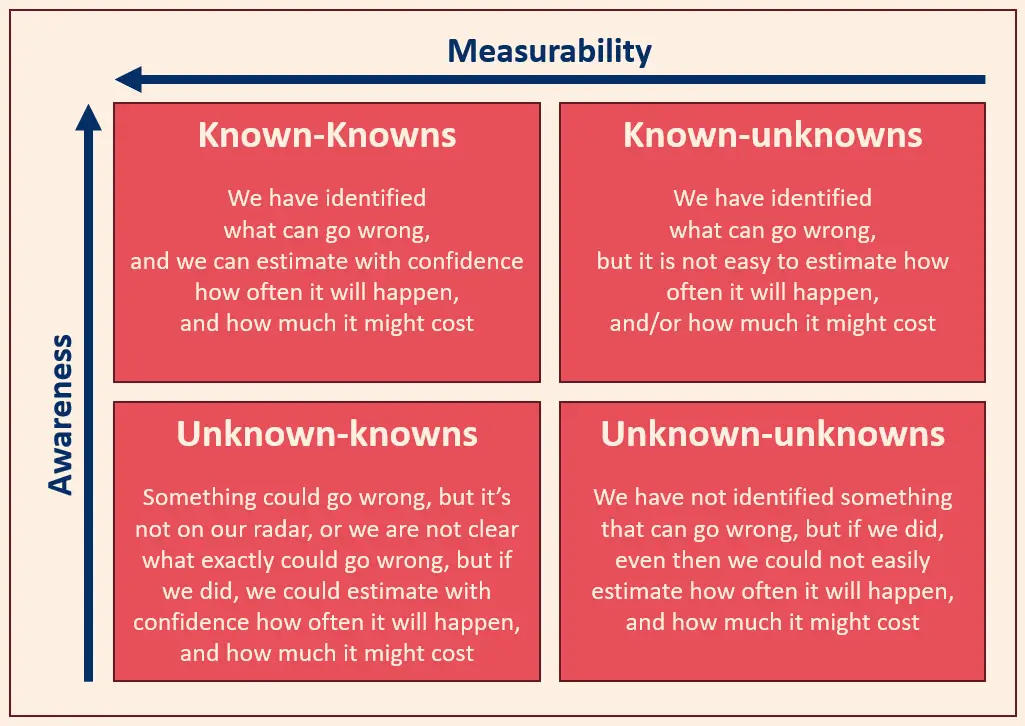
Known-Knowns: Measurable, Actionable, Foundational
These are the risks we understand well and can quantify reliably. Learning from past incident trends is the basis for any mature CRQ model. As low-hanging fruits, these risks can be modelled - accurately, consistently, and with confidence.
Known-Unknowns: Anticipated, But Not Yet Quantified.
Some risks we understand in principle, even if specifics remain unclear. Think zero-day exploits, evolving attacker behavior, or changing regulations.
What to do:
Looking into the so-called “Risk-of-change” like new ransomware tactics or shifts in GDPR enforcement, we’re not aware of what exactly these changes of risks look like, but we can quantify them with the following strategies:
- Learn from other risk profiles: within the large Munich Re risk portfolio, we identify comparable risks to transfer inherent risk patterns and trends to other industries or regions. E.g., the average notification costs per data record from a large incident at a retailer can be transferred to many other industries
- Use of proxy data: e.g., use the long history of business interruption (BI) losses caused by fire to estimate the severity of business interruption caused by cyber incidents
- Large loss case studies: Especially for the few but very severe cyber incidents, our risk experts and loss adjusters learn patterns about failures of security controls and it’s impact on financial consequences to verify or update the model parameters
- Analysis of threat landscape: We monitor threat intel data and early signals to update the model regularly
You don’t need to focus on the causes of incidents, i.e. know exactly when a vulnerability will be identified or exploited, with Squalify’s Top-Down CRQ methodology we focus on the financial consequences. The model in our SaaS platform is pre-populated with frequency and severity parameters based on the data and risk expertise of Munich Re. It’s not necessary to develop and maintain your own model parameters.
These are the “we can’t measure it perfectly, but learn holistically” risks.
Unknown-Knowns: Unlocking What You Already Know
Some risks are already visible to others - or buried within your own systems - but haven’t yet been surfaced. For example, legacy systems no one remembers, forgotten vendor access, tacit team knowledge that never made it into documentation.
What to do:
These are blind spots, the users of Squalify care about, but they don’t need to take actions, because our model parameters are predefined by the Munich Re model which is based on data and loss experience from many other companies which are comparable to yours. This means that you don’t need to exhaustively list every threat scenario that might impact your company; these are built into the model.
Of course, Squalify’s historic data needs to be put into the context of your company. To come up with your company specific quantification results you may provide the following input data:
- Company data: high-level company profile data like revenues and its regional distribution, number of employees, suppliers and datasets describe the risk exposure of your company. Exposure is the inherent cyber risk independently of how you are protected by controls.
- The information security maturity level - measured by any known framework - describes how well you are protected in comparison to your exposure
- The worst case scenarios, identified and quantified by a standardized business impact analysis, provides context about your large loss potential and works as an upper limit for the company-specific loss expectancy curve.
We already have more insight than we think - it’s a matter of turning implicit knowledge into explicit risk data.
Unknown-Unknowns: Designing for Resilience
These are the truly unpredictable events - novel attacks nobody has imagined before, cascading failures, black swan scenarios. While nobody can model them directly, we can make them transparent and prepare for their possibility.
What to do:
- In the Squalify platform we provide transparency on such unknown risks by showing ranges around the financial result metrics
- In addition, we show different certainty scores depending on the data you have entered in the platform
- In our result reports we include statements about what is covered within the model, and what we cannot quantify.
- To at least react quickly to recognized unknown-unknowns, Munich Re invest in an extensive “Emerging Risk Process” to identify early indicators on uncertain risks
Smart users of CRQ models are transparent and realistic about what can be quantified; quantifying with limitations has more value than not quantifying.
Final Words
At Squalify, we recognize that the strongest CRQ model isn’t the one with the most detail - it’s the one with the clearest structure and best data. Results from a CRQ model need trust. And trust doesn’t come from pretending to know everything - it comes from being clear about what you know, what you don’t, and how you’re handling both.
Cyber leaders don’t need perfect visibility. They need frameworks that bring structure to uncertainty, tools that surface hidden assumptions, and reporting that enables board-level decisions - even when the data isn’t complete.
When you build a CRQ model that acknowledges the unknowns, you manage and steer cyber risks with clarity.





