Quantifying cyber risk is no longer a technical exercise reserved for IT teams; it is an essential part of financial and strategic decision-making at the executive level. Cyber incidents can lead to severe financial consequences, ranging from operational shutdowns to regulatory fines. Understanding what drives the financial impact and how to quantify the worst-case cyber scenario, will allow executives to make better-informed investment and risk mitigation decisions.
Why Top-Down Cyber Risk Quantification?
Top-down CRQ starts from the business perspective, not the technical threat landscape. Instead of asking “Which threats could hit us?”, the top-down approach asks “What would the financial consequences be if our operations or data were impacted in the worst possible way?”
Every company operates differently - business models, digital architectures, and supply chain dependencies vary significantly. Because of this, the financial scope of cyber risk must be individually identified for each organization. After identifying the worst-case scenarios in each consequence category, the next step is to quantify financial losses over time.
This blog post builds on the previous articles, “Why Defining Your Worst-Case Cyber Scenario Matters” and “How to Define Worst-Case Scenarios Using a Cyber Risk Methodology” Here, we focus on the next crucial step: quantifying the identified worst-case scenarios.
How to Conduct Top-Down CRQ Quantification
Top-down quantification works from the consequence perspective rather than the causal perspective. With top-down, the potential costs resulting from a cyber incident are looked at if the worst possible incident occurs.
The three major consequence categories quantified by Squalify are:
- Business Interruption
- Data Privacy Breach
- Financial Theft and Fraud
Each category requires an individual quantification approach because losses accumulate differently over time, are driven by distinct cost factors and incorporate different business processes and assets.
What are the Quantification Steps?
When quantifying top-down CRQ scenarios, the process follows three steps.
- First, the worst-case potential financial impact is determined.
- Second, the existing Information Security measures are assessed to understand how well they protect against this exposure.
- Finally, a Monte Carlo simulation is applied to evaluate these protection measures across different consequence categories. This step incorporates Information Security measures to produce a severity distribution and estimate the predicted value-at-risk.
The following sections focus on the first step only: quantifying the worst-case potential financial impact. At this stage, Information Security measures are deliberately ignored. The assumption is that almost all controls fail, and the worst-case financial impact materializes for the given scenario. This perspective reflects the maximum potential financial impact without assigning a probability, offering a useful view of the absolute worst-case scenario a company might face - even if unlikely.
Given the unique nature of each consequence category, the following section examines them individually to clarify how the worst-case scenario could unfold in each case.
Business Interruption
A cyber incident causing business interruption directly halts production or service delivery, most often making it one of the most financially significant cyber risks. Quantifying the financial impact of this scenario requires understanding how the company’s operational structure works, how financial value is generated and what recovery capabilities are available.
Thereby, the quantification does not consider the entire organization, but is scoped to the financial impact of the identified business interruption scenario. For example, in a large manufacturing company, the worst-case scenario could be an outage at the largest interconnected production system, which is typically the main plant, assuming network segmentation prevents broader organizational impact.
Three Phases of a Business Interruption
The financial impact of a business interruption develops in three phases:
- Complete Downtime – Production stops entirely, causing immediate loss of income for a certain duration. Costs for incident detection, escalation, and stakeholder communication also occur during this phase.
- Recovery Phase – Operations resume stepwise, gradually reducing lost profit but still below normal capacity. Lost income decreases over time through additional mitigation efforts. This includes:
- Reserves – Holding reserves to meet demand during downtime helps minimize profit loss.
- Labor Costs – Adjusting or reducing wages limits losses from labor.
- Alternative Production – Using outsourcing, manual work, or substitute machinery can partially maintain production.
- Post-Recovery Phase – Some lost production efforst may be compensated through increasing capacity after resuming pre-incident production levels (make-up production), reducing overall loss. However, not all losses can be recovered, especially for time-sensitive or perishable products.
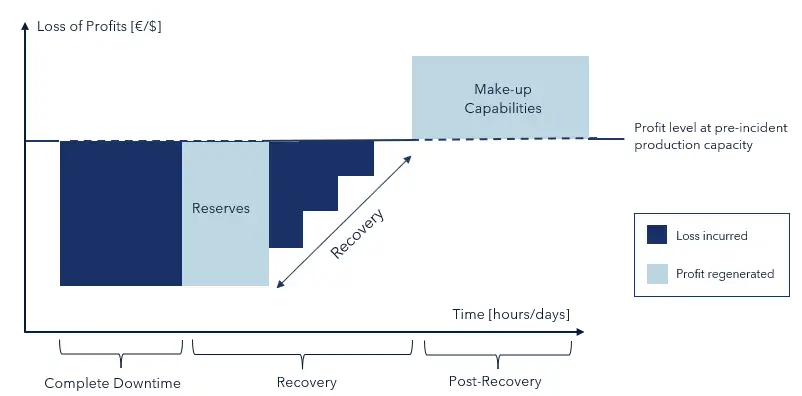
Many costs and assumptions for the impact within every phase of a business interruption, can be gathered through stakeholders within the organization. For instance, the amount of capacity to make-up lost production can be well estimated by the COO. Other figures, such as the per day lost profit can be identified through financial reports or the accounting team.
Combining all these considerations within the three phases, companies can gain a clear understanding of how a cyber incident creates losses over time and how their specific operational setup influences the magnitude of losses.
Data Privacy Breach
A data privacy breach has a very different financial profile compared to a business interruption. Instead of a decreasing loss structure over time, the cost of a breach accumulates over time, with regulatory, legal, and recertification costs as consequences.
Four Phases of a Data Privacy Breach
The financial impact of a Data Privacy Breach scenario typically progresses through four phases, each including a set of different costs. The worst-case scenario, for instance, could involve a breach of a central customer database in a service-based company, exposing sensitive personal data. This assumes that the incident remains contained within that network and does not spread across the organization.
- Detection and Escalation – The process of identifying and assessing the breach quickly to limit damage, such as through forensic investigations, legal consultation, and mobilizing an incident response team.
- Notification – The obligation to inform stakeholders about the breach, including regulators, affected individuals, and the public, for example via hotlines, email alerts, and press statements.
- Post-Breach Response – The actions taken to contain and remedy the breach, often the costliest phase, including regulatory fines, system remediation, legal settlements, and credit monitoring for the affected.
- Lost Business – The long-term financial impact caused by loss of trust, which may result in customer churn, canceled contracts, and delayed or lost future opportunities. This part of the quantification typically involves the most insecure assumptions.
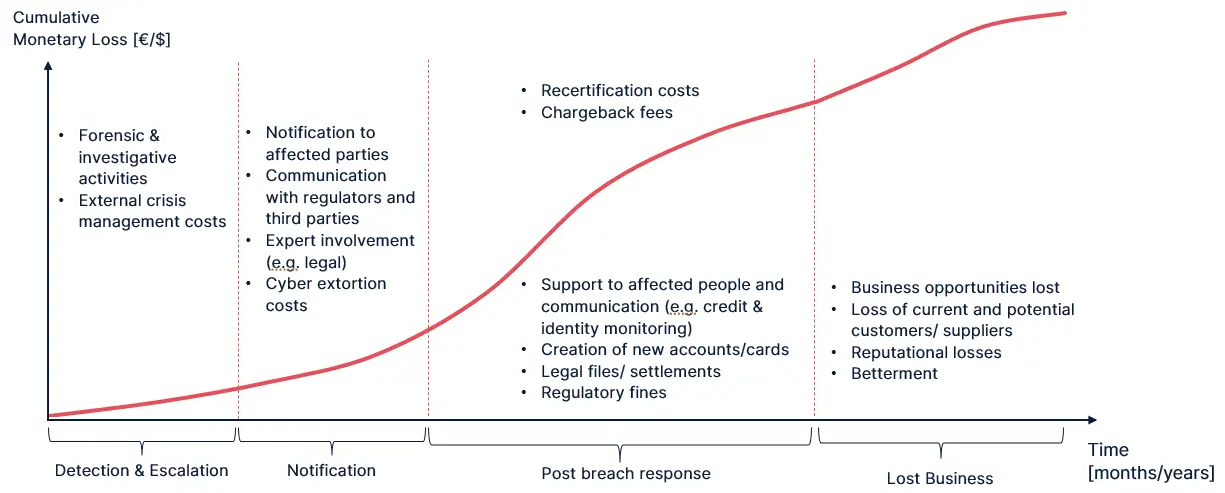
Quantifying the different phases of a data privacy breach scenario requires understanding the specifics of the data within the scenario. Understanding these dynamics is essential for estimating the potential impact.
- Data type & sensitivity – The nature of the compromised data strongly influences costs, with breaches involving sensitive health or financial information leading to higher crisis management costs, fines, settlements and legal costs than those with basic personal data.
- Data volume – The number of affected records drives notification and settlement expenses, although the cost per record often decreases as the volume grows.
- Jurisdiction – The regulatory environment determines penalty severity, with stricter laws such as GDPR or CCPA imposing significantly higher fines.
- Revenue – A company’s revenue affects financial exposure, as fines are frequently calculated based on annual revenue, placing larger organizations at greater risk.
By examining these factors, organizations can better understand the potential magnitude of a breach based on the stored data within different scenarios and the company profile.
The impact estimates for costs within every phase within a data privacy breach can likewise be specified through stakeholders within the organization. For instance, the costs of legal consultants, incident response providers and other third party providers supporting during an incident can be found through consulting provider contracts with the legal team.
Financial Theft and Fraud
Financial theft and fraud presents a more direct form of cyber risk, with immediate monetary losses. While often less complex to calculate than business interruption or data privacy breaches, the potential impact can still be significant, particularly for businesses frequently conducting high-value transactions.
There are two different typical scenarios of financial theft and fraud that are included in the Squalify model, which can be quantified in parallel.
- One-Off High-Value Fraud – Attackers redirect a single large transaction, such as supplier payments, M&A transfers, or dividend payouts. The financial impact in this case is determined by the size of the transaction at risk.
- Continuous Low-Value Fraud – Small amounts are diverted repeatedly over time, often through false supplier invoices or manipulated payroll, until detection. In these cases, the severity depends on an average amount of money typically made and the frequency of these transactions.
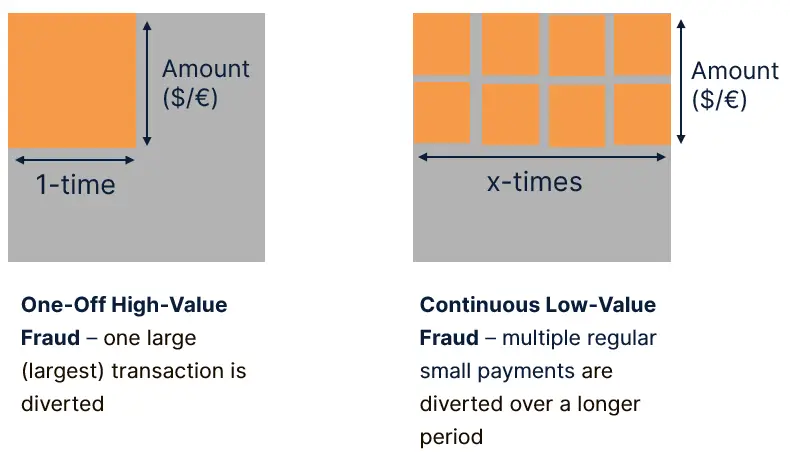
The ease of quantification makes this category different from other cyber risks. The maximum foreseeable loss typically corresponds to the largest at-risk transaction for one-off fraud or the cumulative amount that could be stolen before detection in a continuous fraud scheme.
For many organizations, improving approval measures and monitoring systems can drastically reduce this risk, making financial theft and fraud a category where prevention is often highly cost-effective compared to potential losses.
Conclusion
Quantifying cyber risk is not just about assigning numbers; it is about understanding how financial losses develop differently across consequence types. A top-down CRQ methodology allows executives to gain this understanding quickly and holistically, focusing on the most financially relevant scenarios.
By assessing business interruption, data privacy breaches, and financial theft & fraud individually, leaders can:
- Communicate cyber risk in financial terms stakeholders understand.
- Prepare for worst-case scenarios with clear, fact-based reasoning.
- Provide an aggregated, enterprise-wide view on cyber risk.
Cyber risk is ultimately business risk, and understanding its potential financial impact is key to making resilient, strategic decisions.









