If you're reading the IBM Cost of a Data Breach 2025 and thinking "$4.4million seems pretty low for the average cost of a data breach", you're not wrong.
Maybe you recall the headlines reporting the costs from the Change Healthcare breach reaching over two billion dollars, or Equifax settling with the FTC for $575million.
Maybe you’ve discussed these cases with your Board.
And now the new average cost is an order of magnitude lower?
The IBM number is not wrong, but it doesn’t give you the full picture.
The dangerous limitation of the IBM Cost of a Data Breach Report
You have to get to page 57* of the Cost of a Data Breach Report to see the most significant, and I'd argue dangerous, caveat in the FAQ section:
Can the average per-record cost be used to calculate the cost of breaches involving millions of lost or stolen records?
It’s not consistent with this research to use the overall cost per record as a basis for calculating the cost of single or multiple breaches totaling millions of records. The per-record cost is derived from our study of hundreds of data breach events in which each event featured a maximum of 113,000 compromised records.
The IBM average cost is based on a maximum of a little more than one hundred thousand records being breached.
The IBM average cost of a data breach does not include mega breaches
All of the mega-breaches reported in 2024 and no doubt capturing board room attention are not included in the IBM Cost of a Data Breach
- Change Healthcare (100million+ records) - NOT INCLUDED
- Dell (49million records) - NOT INCLUDED
- Ticketmaster (40 million records) - NOT INCLUDED
The IBM average cost of a data breach provides a low anchoring point
The IBM report and average cost of a data breach is one of the most widely quoted figures in cyber security.
The headline figure is frequently quoted in articles alongside examples of mega-breaches without clarifying that all the mega-breaches in the article are beyond the scope of the average cost in the IBM report.
Knowing that large breaches may exceed this average cost by an order of magnitude means that the oft-quoted $4.4M average cost can introduce a dangerous anchoring bias when discussing quantified cyber risks.
Using the IBM average cost of a data breach could mean you massively underestimate the costs of a data breach
Now, you might argue that these mega-breaches are outliers and rightfully excluded from the average costs.
I would argue that it’s important to understand the probability of such large losses; while relatively unlikely it is nonetheless important that businesses understand these risks and decide how they wish to manage them.
If you're using the $4.4M value as an average cost for your risk calculations you may be massively underestimating the cost of a worst case scenario. Especially if you have more than 100,000 records.
If this figure comes up in your discussions in the Board room, you are now ready to remind people that this average costs only takes into accounts breaches with up to a hundred thousand records.
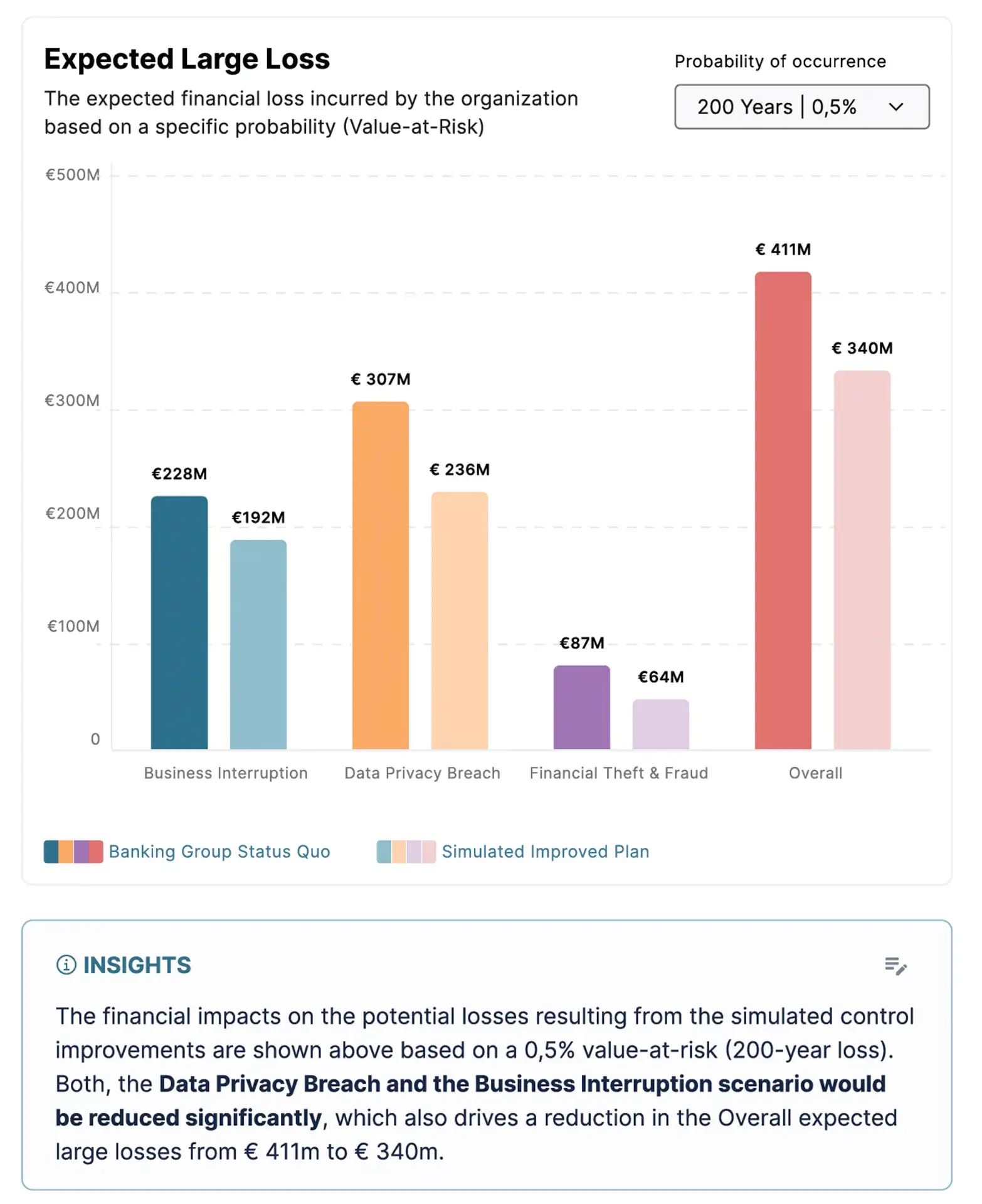
How Squalify can help you see the full costs of a potential data breach
The Squalify Cyber Risk Quantification platform provides you the tools you need to quickly and easily calculate the potential costs of cyber security incidents.
In addition to the costs of an average breach, we also model the costs of large breaches and the probabilities of these. This enables decision makers to see the full picture and take data-informed decisions for cyber risk management.
To find out more about approach, check out our Top Down Cyber Risk Quantification White Paper.
*Note - the maximum size of the breaches in scope is included in the Executive Summary, but the implications of it are not spelled out until the end of the report.









