I have written previously about the relationship between the CISO and the Board, how the CISO can better understand the Board’s role, and improve the reporting of cyber topics to the Board.
This blog post builds on that to discuss common questions that the Board will ask of a CISO, and how a CISO can successfully navigate the ensuing discussion.
Not only risk, but also opportunity management
McKinsey recently noted that “Corporate boards and the C-suite used to think of cyber-risk management as an investment in avoiding loss—of data, money, and, importantly, trust. That view has evolved, and today cybersecurity is increasingly recognized as a driver of competitive advantage and critical-asset protection.”
We must move beyond the language of technical threat avoidance into a balanced discussion of operational negative risk (loss, damage, liability) and strategic positive risk (opportunity, innovation, market capture, competitive advantage).
The Board of Directors has a fiduciary responsibility to govern both: enabling the organisation to grow by seizing value-creating opportunities presented by emerging technologies, while being aware of and overseeing efficient and effective management of risks.
Lead the dialogue
The following table summarises the topics that are typically on a Board’s mind, suggests ways that a CISO could answer these questions, and also gives ideas for how a Board could probe deeper.
Keep the momentum going
More and more CISOs are getting time with the Board. The challenge for us is to maintain this momentum. Keep the conversation alive between board meetings. Bring stories of wins (not just warnings) and frame every risk discussion alongside the opportunity it protects. Show that security is not just keeping pace with the business, but enabling it to move faster with confidence.
How Squalify can help
Squalify’s cyber risk quantification platform is designed to be intuitive for presenting insights to a board level audience, while also being easy for analysts to use. We focus on strategic metrics, quantifying cyber risk in financial terms, and reporting cyber risk in terms of business impact scenarios, rather than deeply technical KPIs.
Our unique top-down cyber risk quantification methodology focuses on easy to obtain information, and our model is trained on historic cyber loss data, meaning that analysts spend less time estimating threat event frequencies.
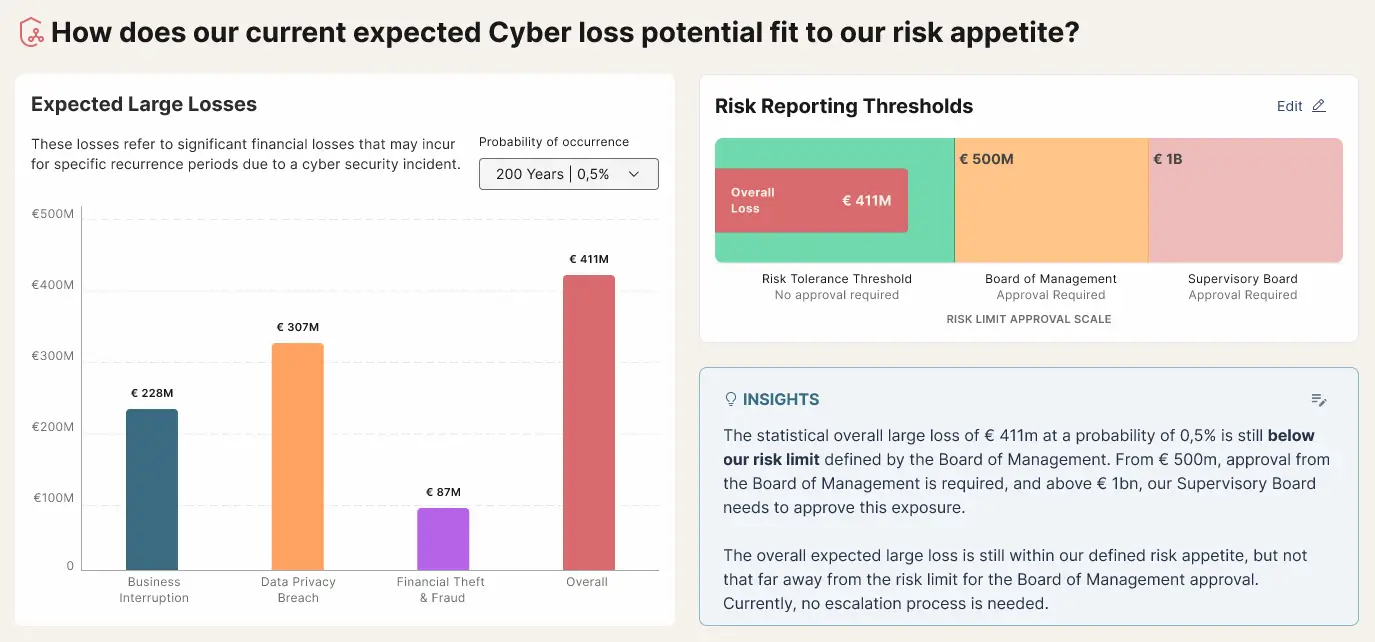
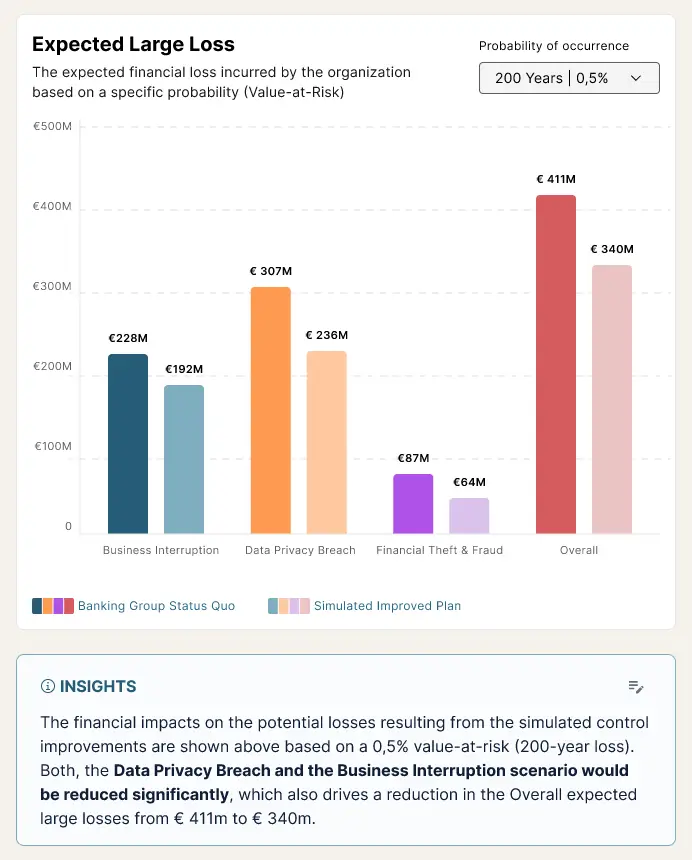
The Squalify platform can also be used to simulate the risk reduction impact of improving security controls. Instantly model and compare multiple investment scenarios to identify the most effective strategies, and prepare for budget discussions with the Board. Quantify the financial impact of each risk mitigation option and determine the best approach to balance cost, risk, and business objectives—before making a commitment.
For further details on how Squalify translates cyber risk into business impact, check out this blog post.








